Hack 17. Manage Digital Certificates
Who gives Firefox trustworthy advice? You can change that set of advisors. All content from a web site that advertises itself as secure has to be checked. Secure content must be accompanied by a digital signature and by a certificate that says whom the digital signature belongs to. The certificate must originate from a Certificate Authority (an organization) that Firefox knows. This hack explains how to change the certificates and Certificate Authorities (CAs) that Firefox knows about. 2.8.1. Examining Existing Certificates and AuthoritiesThe Firefox Options dialog box lets you manage digital certificates. Click the Advanced icon to display that panel, expand the Certificates item, and click the Manage Certificates... button. Figure 2-3 shows that window, with the fourth tab in front. Figure 2-3. Default certificate authority certificates in Firefox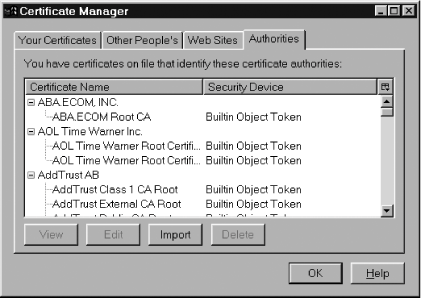 If you click on any of the rows labeled Builtin Object Token, you can then examine the certificate by pressing the View button or limit its use via the Edit button. All of the certificates listed are bundled with the standard Firefox install. There's little reason to delete them, but you can if you want. If you do so, that will restrict the number of secure web sites that Firefox can successfully visit. You can also list these certificates from outside Firefox. Copy these files from the current Firefox profile to a temporary directory: cert8.db key3.db secmod.db All three files (cert8.db, key2.db, and secmod.db) are required. To see their contents, use signtool [Hack #18], like this: signtool -L -d"."These three files contain, respectively, certificates, public-key encryption keys, and a list of security modules that provide enabling regimes for browser security. An enabling regime is just a starting point for security. The alphabet soup that describes such regimes includes PKCS #11 and PSM standards. Implementations of those standards make up the default (built-in) security regime for Firefox. Other regimes that could be added (via additional software libraries) include systems that support smart cards and dongles. The other tabs in this dialog box contain these details:
2.8.2. Adding More CA CertificatesCertificates are defined by a range of standards, collectively called X.509. You can add authoritative CA certificates to Firefox at any time. The first step is to establish the credibility of the CA you're going to add. Don't assume that all CAs are credible. Free software exists that lets anyone set themselves up as a CA. Once the CA has delivered (for free) its root certificate, import it. To import via the GUI, click the Import button in Figure 2-3 and supply the certificate file. Firefox thinks files with the following extensions are certificates, but you can identify the file by hand (the extension isn't important): .crt .cert .cer .pem .der The file should be in either in DER or (old Netscape) Base-64 encoding. Firefox can handle chained certificates stored together in one file, but it might not display all of them before final import. To import direct from the Web, make sure the CA certificate is served up with this content type: application/x-x509-ca-cert Use this alternate type for web server certificates: application/x-x509-server-cert To import certificates using the command line, work on copies of the cert8.db, key3.db, and secmod.db security files with the certutil tool that is bundled with signtool. Here's a suitable command-line argument: certutil -A -n "nickname" -t c -d "." [ -a ] -i new_ca.cert Use the -a option for Base-64-encoded certificates only. Note that the -d option requires a space before its argument. Copy the files back to Firefox afterward. 2.8.3. Rejecting Certificates with CRLs and OSCPIf a certificate owner loses his credibility, he shouldn't be allowed to use his certificate anymore. Somehow, the browser user needs to find this out. The browser displays a warning if it detects a trust request that uses a bad certificate. But how does the browser know? Certificate Rejection Lists (CRLs) are one solution. CRLs are files with formats defined in RFC 2459. Each list is a set of certificates that a particular CA wishes they could revoke. Firefox checks all installed CRLs when signed content requests user trust. None are installed by default. If you have all the CRLs from all of the CAs Firefox knows about, then the number of bad folks you'll accidentally trust is much reduced. One problem with CRLs is that they get out of date. Every CRL should be brought up to date frequently. Firefox can do that either at set expiry times in the future or at a fixed regular frequency. The default frequency if any CRLs are installed is 30 seconds. Some update information is also stored in the preferences system, but the details are too gory for this hack. To collect all the CRLs you need, visit the web sites of all CAs known by Firefox. Click on all the links to CRLs at those sites. CRLs are then downloaded and installed. They're detected using this content type: application/x-x509-crl You can also import a CRL from a file if the CA delivers it to you as an email attachment. A second solution to bad certificates is Online Certificate Status Protocol (OCSP). If it's enabled, Firefox won't check CRLs each time trust is requested by signed content. Instead, Firefox will send a request to the URL specified when OCSP was turned on. The server at the other end (or a proxy server) will report if the trust request includes a safe certificate or not. If it is, the original content will be trusted. That's a lot of extra network overhead for a dial-up connection, though. |