Before discussing various honeypot solutions in detail, we must examine some of the tools that can be used to probe and scan honeypots. The tools discussed in this section are primarily used for perimeter reconnaissance and network traffic monitoring. Attackers would often like to know what kind of target they are up against. Before attacking a host, they collect information about the operating system and what kind services are running on it. Knowledge about the operating system is really important to understand what vulnerabilities the host might exhibit. Information about services and their respective versions allow the adversary to plot a route of attack. In our case, it is really important to understand how nefarious minds might try to break into our honeypots, and that is why we want to cover these tools in detail. One tool that belongs in everyone's toolkit is called Nmap, and it has become so popular that it was even featured in the movie The Matrix Reloaded.
Understanding the output of some of these tools can be quite complicated. If you are not familiar with TCP and did not read the sections on networking, you might want to skip the discussion of tcpdump and Ethereal and come back to them later.
The primary tool to understand what is going on in the network is called tcpdump. Tcpdump is capable of sniffing the network and presenting the data in an understandable fashion. Using a powerful filter language, tcpdump can be used to show network traffic only for hosts and events interesting to us. The official website of the tool is http://www.tcpdump.org/, where you can also download it. Most Unix-based systems ship with a version of tcpdump, or you can simply install it via the package management system. WinDump is the Windows version of tcpdump and available at http://www.winpcap.org/windump/.
To capture traffic going to and leaving from 10.0.1.91, we run the following command:
# tcpdump -n -s 1500 host 10.0.1.91
Figure 1.2 shows the result of running the command against some saved sample traffic. First, some ARP messages are used to map an IP address to a given MAC address. Then, a TCP connection between host 10.0.1.91 and 10.0.1.6 is established via the TCP handshake. A few data packets are sent before the connection is terminated via FIN packets. A good understanding of TCP/IP is required to make the best use of tcpdump. However, just figuring out if a honeypot is up and accepting connections does not require much skill and should be easy once you have read this section.
|
Code View: reading from file /tmp/dump, link-type EN10MB (Ethernet)
19:34:35.54 arp who-has 10.0.1.91 tell 10.0.1.6
19:34:35.54 arp reply 10.0.1.91 is-at 00:90:27:a0:77:9b
19:34:39.40 IP 10.0.1.6.2809 > 10.0.1.91.25: S 317611736:317611736(0)
win 5840 <mss 1460,sackOK,timestamp 111830 0,nop,wscale 0>
19:34:35.55 arp who-has 10.0.1.6 (ff:ff:ff:ff:ff:ff) tell 10.0.1.91
19:34:35.55 arp reply 10.0.1.6 is-at 00:09:5b:be:66:92
19:34:39.40 IP 10.0.1.91.25 > 10.0.1.6.2809: S 2544916314:2544916314(0)
ack 317611737 win 5752
<mss 1460,nop,nop,timestamp 213261 111830,nop,wscale 0>
19:34:39.40 IP 10.0.1.6.2809 > 10.0.1.91.25: . ack 1 win 5840
<nop,nop,timestamp 111833 213261>
19:34:39.40 IP 10.0.1.91.25 > 10.0.1.6.2809: . 1:90(89) ack 1 win 5752
19:34:39.40 IP 10.0.1.6.2809 > 10.0.1.91.25: . ack 90 win 5840
<nop,nop,timestamp 111836 213261>
19:34:42.39 IP 10.0.1.6.2809 > 10.0.1.91.25: P 1:17(16) ack 90 win 5840
<nop,nop,timestamp 114826 213261>
19:34:42.39 IP 10.0.1.91.25 > 10.0.1.6.2809: . ack 17 win 5736
19:34:42.40 IP 10.0.1.91.25 > 10.0.1.6.2809: . 90:163(73) ack 17 win 5752
19:34:42.40 IP 10.0.1.6.2809 > 10.0.1.91.25: . ack 163 win 5840
<nop,nop,timestamp 114830 213261>
19:34:44.63 IP 10.0.1.6.2809 > 10.0.1.91.25: P 17:23(6) ack 163 win 5840
<nop,nop,timestamp 117066 213261>
19:34:44.63 IP 10.0.1.91.25 > 10.0.1.6.2809: . ack 23 win 5746
19:34:44.64 IP 10.0.1.91.25 > 10.0.1.6.2809: F 163:163(0) ack 23 win 5752
19:34:44.64 IP 10.0.1.6.2809 > 10.0.1.91.25: F 23:23(0) ack 164 win 5840
<nop,nop,timestamp 117071 213261>
19:34:44.64 IP 10.0.1.91.25 > 10.0.1.6.2809: . ack 24 win 5752
|
This section briefly reviews the most important flags to tcpdump and some of the features of the pcap filter language. For anyone who needs to know all possible commands like flags or more details about the filtering language, tcpdump comes with a fairly usable man page. The following flags are the ones you are most likely to use:
-i interface: Selects the network interface from which tcpdump is capturing traffic. The default is your primary Ethernet interface like en0, but sometimes if your machine has more than one network interface, you might want to listen to a different one.
-n: Turns off DNS resolution and displays the IP addresses instead. This flag is useful if you are monitoring a busy server that is getting connections from all over the world. If tcpdump has to resolve the DNS names for all of the new IP addresses, the output can be delayed significantly. Also, if you are not currently connected to the Internet and are experimenting on a local network, this option comes in handy.
-s snaplen: By default, tcpdump looks only at the first 64 bytes of the packet. This makes processing very fast, but for some protocols the data is not sufficient to completely decode the packet. By setting the snap length to 1500, whole packets can be captured and inspected.
-X: When this flag is turned on, tcpdump displays the contents of the packets in hexadecimal and in ASCII for printable characters. This is very useful to quickly look at the contents of a packet and see what kind of data is being transmitted.
-S: Prints the absolute value of sequence numbers. By default, tcpdump displays the difference in sequence numbers counting up from the sequence number of the first captured packet in a connection. It sometimes helps to turn this off.
-w filename: Dumps the captured packets into the specified file. This feature is very useful if you plan on thoroughly inspecting the captured packets later or if you keep them for forensic analysis. The size of the file can increase quickly if you are monitoring a busy network.
-r filename: Reads a previously saved dump file and prints the network data just as if it was directly obtained from the network. To read data from stdin, the filename "-" can be used.
To have a more convenient interface, you can also use the tool Wireshark (formerly known as Ethereal). Wireshark gives you the same amount of information as tcpdump, but you have a graphical user interface, so it is often much easier to analyze a given packet trace.
The official website of Wireshark is http://www.wireshark.org/, where you can download the tool for many different platforms. It is available for Windows in both binary and source code format and also for different Linux distributions and BSD variants. Moreover, a version for Mac OS X is also available.
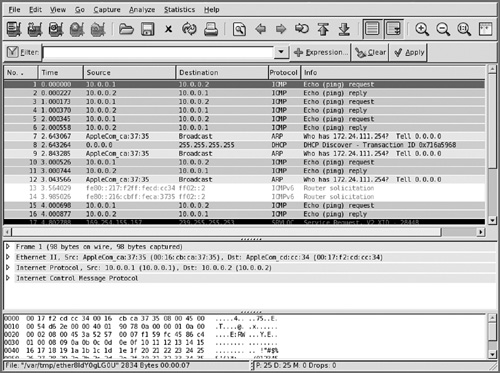
Figure 1.3 provides a screenshot of Wireshark. You can see that ICMP packets are sent between two hosts and also some other packets captured in the network. Each packet is displayed in its individual sections, and you can analyze all packets in great detail.
Nmap is defined by its author, Fyodor, as a network exploration tool and security scanner, which is really a euphemism for operating system fingerprinter. With Nmap we can quickly scan a number of hosts on the Internet to figure out which operating system they are running and which services they are offering. To determine the operating systems and services running on 192.168.1.1, we invoke Nmap as a root user with the following command:
nmap -sS -O -F 192.168.1.1
The output in Figure 1.4 informs us that 192.168.1.6 runs a recent version of the Linux kernel. Nmap cannot quite tell which one, so it gives us a choice between Linux 2.4.18 and Linux 2.6.7. The version numbers correspond to the kernel version that the hosts runs. Each kernel might choose to implement TCP slightly differently, and Nmap uses these differences to determine the operating system a host is running. In this case, the scanned Linux host was indeed running 2.6.7. It is interesting to see that other TCP artifacts, like TCP timestamps, allow Nmap to determine how long the machine has been running. In this case, the host has been up for just under one hour.
|
Code View: Starting nmap 4.11 ( www.insecure.org/nmap/ ) at 2007-01-16 17:45 PDT Interesting ports on 192.0.2.1: (The 1208 ports scanned but not shown below are in state: closed) PORT STATE SERVICE 9/tcp open discard 13/tcp open daytime 21/tcp open ftp 22/tcp open ssh 23/tcp open telnet 25/tcp open smtp 37/tcp open time 79/tcp open finger 80/tcp open http 111/tcp open rpcbind 113/tcp open auth 139/tcp open netbios-ssn 445/tcp open microsoft-ds MAC Address: 00:09:5B:AF:34:11 (Netgear) Device type: general purpose Running: Linux 2.4.X|2.5.X|2.6.X OS details: Linux 2.4.18 - 2.6.7 Uptime 0.033 days (since Tue Jan 16 16:57:58 2007) Nmap finished: 1 IP address (1 host up) scanned in 3.883 seconds |
A very detailed installation manual for Nmap is available at http://insecure.org/nmap/install/. The tool is available for all major platforms, including Windows, Linux, and the BSD variants. You can either install it as a binary or compile it from source code.
Nmap is a really complex tool, and we just want to give a brief overview of the most commonly used command line flags:
-sV: Enables version detection — that is, Nmap tries to identify which service is running with which version on a given port.
-O: Enables detection of the remote operating system
-A: Enables version detection and OS detection
-T[0-5]: Sets the timing option; a higher number means less time between two probes.
-oN/-oX/-oG file: Specifies the output format as normal, XML, and grepable format, respectively. The scan report is written to the file, and you can use it for later analysis.
These six command line flags should be sufficient for everyday use of Nmap. The tool is especially helpful if you want to verify that your honeypots are up and running. You can also determine whether all services are running.