VMware, Inc. offers a variety of virtualization software solutions and is currently one of the most advanced players in this field. Virtualization software means that the software emulates a complete x86-based computer system and offers the possibility to run one or more operating systems within this virtual machine. In the following, we will refer to the products offered by this company simply as VMware. In principle, all of the following content can also be applied to other kinds of virtualization software solutions like Microsoft Virtual PC or Parallels Workstation/Desktop. For the sake of simplicity, we focus on VMware and point out differences if they exist.
In the remainder of this chapter, we differentiate between the host system and guest system: The computer and operating system instance that executes the VMware process is referred to as the host machine. This is your physical machine on which you install VMware. An operating system running inside a virtual machine is referred to as a guest system or a guest virtual machine. The interaction between these two kinds of systems can be rather transparent. For example, it is possible to share folders and copy and paste text and files between the host and guest system with VMware. We will always point out whether you must execute the commands on the guest or the host system.
We used the term virtual system already, but what exactly does it mean? The host machine shares the CPU and memory resources with the guest virtual machines. Like an emulator, VMware provides a completely virtualized set of hardware resources to the guest operating system. For example, each of your guest systems will have the same graphics adapter and the same network interface, regardless of the actual physical graphics adapter or network interface of the host system. Besides these two devices, VMware also virtualizes hard disks, floppy drives, and DVD/CD-ROM drives for the guest system. Moreover, the sound adapter, a USB controller, and serial and parallel ports are enabled as a pass-through driver to the host system. Figure 2.1 provides a schematic overview of VMware's architecture. The system is (almost) fully equivalent to a physical host. And within the virtualized hardware, can be installed any operating system that can be installed on an x86-based machine — that is, an ordinary Intel or AMD processor.
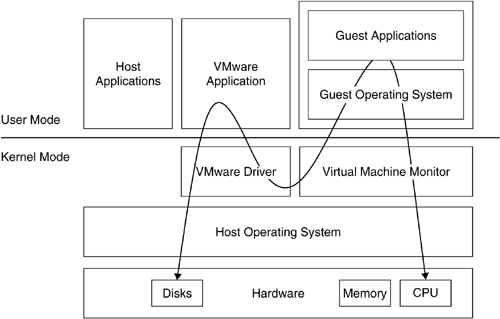
VMware is capable of running many different versions of Windows, starting from Windows 95 up to Windows Vista. In addition, the guest system can be Linux, most of the BSD family, Solaris for Intel, Novell NetWare, and some other operating systems. Not all of them are officially supported, but it is nevertheless possible to run them. Please note that you cannot execute operating systems that require a non-x86-based processor, such as a Sun SPARC processor or a processor from the IBM PowerPC family. At the time of this writing, it is not possible to install Mac OS X within VMware.
However, there are a variety of virtualization options available for Mac OS X. VMware offers a product called VMware Fusion that allows you to create virtual machines on a Intel-based Mac. In addition, Parallels Desktop (http://www.parellels.com) is another tool that offers similar functions. This virtulization software is also available for Intel-powered Macs. Moreover, Virtual PC from Microsoft also support a variety of different operating systems, so you are rather flexible on which OS should run on your honeypot.
Regarding performance and scalability, all products offer similar possibilities. The guest systems usually achieve a performance that is slightly lower when compared to a native system, but this is not crucial for a honeypot. After all, the honeypot has no real value within your environment and is used for detecting attacks. Even if the performance is only 50 percent of the native speed, that is enough to learn more about attacks. The scalability depends on the configuration of the host system. For each virtual machine, you should budget at least 256MB RAM or, even better, 512MB. This is the amount of memory the virtual machine will use, and most operating systems require at least that much. In addition, you also need memory for the guest system. For example, if you plan to have three virtual machines running Linux and a host virtual machine running Windows XP, you should have at least 3 x 256MB + 1 x 512MB = 1280MB of RAM. The CPU is also important. Since the virtual machines and the host system share the CPU, you should plan to buy a faster CPU to achieve good performance.
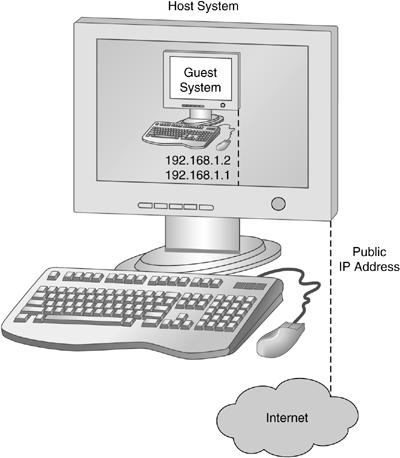
A guest virtual machine will become our honeypot. Figure 2.2 illustrates this differentiation. The picture gives an overview of the virtual high-interaction honeypot that we will set up during this section. The host system is your physical machine on which we install VMware. The system in dark gray is the guest virtual machine that is running within a simulated environment. As you can see, we are going to configure this honeypot with an IP address from the private network range as defined in RFC 1918 (IP address 192.168.1.2 in dark gray for the guest system). This means that the honeypot in this configuration will not be reachable from the Internet. It serves just for testing purposes and to familiarize you with the concept of high-interaction honeypots. At the end of this section, we show how to change the configuration so that the honeypot is also reachable from other hosts on the Internet. Afterward, your honeypot is "live" and can also be attacked by adversaries from all over the world. At that point you start to collect real information about cyber attacks against your honeypot.
You should be aware that VMware is a commercial solution. However, VMware, Inc., also offers some versions of the software that you can download and use for free. We continue this section with some background information on the different versions of virtualization software by VMware and then continue with the installation process.
Currently, VMware, Inc., offers several solutions of virtualization software. As just noted, some of them are commercial, and some of them can be used for free. The following four solutions are something to consider when you use VMware to build a virtual honeynet:
VMware Player is the entry version to get familiar with the concept of virtual machines. You can download this software for free at http://www.vmware.com/download/player/, and later we show you how to configure and use it. The restriction of this tool is that it cannot create virtual machines by itself; it can only start and run a given guest virtual machine. However, there is a trick to creating virtual machines with the help of a third-party solution, which is introduced in Section 2.2.4. But there also exist many preconfigured virtual machines that you can just download and execute.
VMware Workstation lets you build your own guest virtual machines. Moreover, it is possible to create multiple snapshots that save a particular state of the virtual machines. This enables easy maintenance of your virtual honeypots, since you can easily revert to a clean version once an adversary has compromised a machine. This version is only available for purchase, but you can download a 30-day evaluation version from the VMware website at http://www.vmware.com/products/ws/.
VMware Server (formerly VMware GSX Server) is the next bigger version. It aims for server virtualization technology — for example, to partition a physical server into multiple virtual machines. Since the beginning of 2005, VMware, Inc., has offered its former GSX Server version for free as VMware Server. Compared to the VMware Workstation, the snapshot features are limited to only one snapshot per virtual machine. More information is available at http://www.vmware.com/products/server/, where you can also find a link to download the software. We cover the installation and configuration process in this section.
VMware ESX Server is the high-end version of virtualization software available. If you want to build very large virtual honeynets with only limited requirements in hardware, you should consider this version. It is optimized for enterprise data centers, and you can find detailed information at http://www.vmware.com/products/esx/.
We will focus on VMware Player and VMware Server, since these two versions are available for free. For the guest virtual machine, we prefer Windows 2000 for two reasons. First, a Windows honeypot has a high chance of being compromised in a short amount of time. This will give you instant feedback when you set up a high-interaction honeypot. You will quickly learn whether this is the right tool for your work. Second, a Windows honeypot can also be used for some other purposes, such as to analyze a given malware binary. For now, this is not very important, but we will introduce several applications of high-interaction honeypots in later chapters for which Windows-based honeypots are useful. If you want, you can also use other operating systems for your virtual honeypots. In general, the steps outlined in this chapter can be applied to other operating systems, and we mention differences where necessary. Once you are familiar with the concept of high-interaction honeypots, you will most likely want to run different kinds of honeypots.
Before starting the installation process, it is important to examine the different possibilities of a virtual network. Our honeypots need to have network access, since we want to learn more about cyber attacks. Up to three virtual network cards can be configured in each virtual machine. Each of them appears to the guest system as a generic Ethernet card with the model AMD PCNet II. You can configure these virtual interfaces like a real network interface; the virtual network is transparent for the guest virtual machines. VMware offers four different ways to configure a virtual network between the host system and the guest virtual machines. Of course, it is also possible to configure no network at all, but this is useless for a honeypot setup because you want your honeypot to be accessible from other machines.
These are the four different methods:
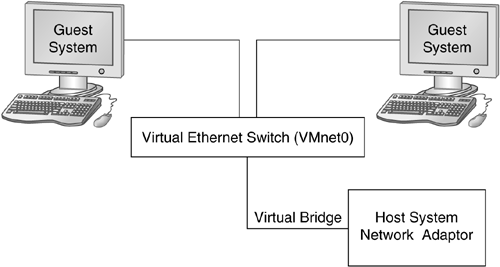
Bridged networking (default mode): In this setup, the host system acts as a transparent bridge for the guest virtual machines. The schematic overview of this setup is given in Figure 2.3. All virtual honeypots have their own MAC and IP address and thus appear as an entirely separate machine on the network. You can either configure the IP address of the virtual machine yourself or use DHCP (Dynamic Host Configuration Protocol) within your network to automatically assign an IP address to the interface. The virtual network interface of a guest virtual machine interacts with the host's network interface and uses it to send its packets to the local network. The host system routes all packets destined for the virtual machines to the correct one. The whole process is transparent for the virtual machines — that is, an adversary cannot (almost) distinguish whether the host is running as a virtual machine.
NAT network: If you cannot assign an IP address of the external network to your guest virtual machines, you can use network address translation (NAT) to easily enable network access for your virtual machines. In this setup, the host system acts as a gateway for the virtual network in which the virtual machines are hosted. This means that the guest systems share the IP address of the host system. A DHCP server within the virtual network assigns an IP address to the virtual systems. The network range of this virtual network belongs to a private IP range as defined in RFC 1918 — for example, to 192.168.1.0/24. During the installation phase, the installer can check for a free private IP range within your network. So if you have no clue what the right network range is, just let the installer choose one for you. The main drawback of this solution is that the virtual machines are not easily reachable from the Internet because they reside within a private IP range. For a virtual honeynet, such a setup is thus only suitable for testing purposes. Nevertheless, we will first configure our virtual honeypot with NAT mode to test and evaluate the setup.
Host-only network: In this setup, the guest virtual machines and the host system belong to one network and are not connected to the Internet. The individual virtual machines can contact the host system and multiple virtual machines can talk to each other as well. However, no packets are forwarded to the local network as in the NAT mode. The virtual network is thus completely contained within the host computer. A DHCP server assigns IP addresses to the virtual machines in this isolated network. This setup is also only suitable for testing and analysis purposes. During the installation phase, the installer can again choose a network range that you can use. So if you are unsure, let the installer choose a network range for you.
Custom mode: When you want to set up a complex network on your own, you can use custom mode. For example, if you want to configure several virtual machines using several private virtual networks, you should use this option. Configuration of custom networking requires a good understanding of networking concepts and potentially the implementation of some simple user-level applications. We will not cover this option in details, since NAT and bridging mode offer all the flexibility we need to set up a virtual honeynet.
When VMware is installed on your computer, the host system will have a few additional network interfaces. By default, each of the first three networking options creates network interfaces that correspond to the different network modes. On Linux, these interfaces begin with the names vmnet: vmnet0 is dedicated to bridged mode, vmnet1 is dedicated to host-only mode, and vmnet8 is for NAT mode. Six additional interfaces (vmnet2–vmnet7) are available if you choose to have custom networking mode. On Windows, these additional interfaces are also available with the same name.
There are two things you should be aware of. First, in bridged mode, the virtual machines use vmnet0, which by default maps to the first available network interface (eth0 on Linux). If you have more than one physical network card in your host system, you should manually map the virtual and physical network interfaces.
Second, in NAT mode, you can establish a connection between the host virtual network interface and a physical network adapter on the host system. This allows you, for example, to connect the virtual machine to a non-Ethernet network. To use this feature, you have to configure the host system accordingly: For Windows as host system, use the Internet connection sharing (ICS; available under Control Panel, Network Connections) option. For Linux, you must enable the IP forwarding option with the help of the command
$ sudo echo "1" > /proc/sys/net/ipv4/ip_forward
For further references and extensive documentation, we recommend that you take a look at the official documentation available at http://www.vmware.com/support/pubs/.
Now that we have seen the basics of VMware, we will take a look at the actual installation and setup process. As just noted, we will guide you through the process of setting up a virtual honeypot based on VMware Player/Server and Windows 2000 Professional. This virtual machine can then be used as the basis for your experiment with honeypots.
Some prerequisites have to be met by your host system. It should have at least 512MB of RAM to run virtual machines without too much swapping. We recommend at least 1GB of RAM or even more for better performance. Remember that the host system and the virtual machines share the resources of the physical system, so more RAM is even better. A modern processor offers enough performance to execute even several virtual machines in parallel. We recommend that your processor has at least 1GHz to have decent performance. Moreover, you should have at least 4GB of hard disk space for each virtual machine. Your host operating system must be either Windows or Linux. If you want to install the Linux version, please make sure that you have installed a developer environment — that is, a compiler (usually gcc), a linker (usually ld), and additional tools should be installed. Furthermore, you need the kernel header files according to your running Linux version. Please consult the documentation of your Linux distribution if you are unsure.
VMware Player, the software capable of running preconfigured virtual machines, is the entry solution, and we cover the installation process first. Setting up VMware Player requires only a few steps:
1. | You find the download link at http://www.vmware.com/download/player/. You should fill out a short survey to provide some feedback to VMware Inc. Next, read and, if applicable, agree to the end user license agreement (EULA) before starting the download process. The EULA states that you can use this software "solely for your own internal information processing services and computing needs." In addition, you must have written permission from VMware, Inc., if you want to distribute the software. Please read the EULA yourself to learn more about further details. |
2. | Choose an appropriate version of VMware Player. If you want to run the software with guest system Windows, please choose the .exe version. For running it under Linux, you can either choose an RPM-package (suitable for Red Hat, Fedora Core, and other RPM-based distributions) or download the tool with its source code as a tar.gz-ball. |
3. | Depending on the version of VMPlayer you are going to use, do one of the following:
|
No further configuration is necessary, since all the steps have already been covered during the installation process. If you want to change the configuration under Linux, execute the command
$ sudo /usr/bin/vmware-config.pl
and follow the on-screen instructions.
To start the VMware Player under Windows, double click on the icon, and then the software will start up. For Linux, execute the command
$ /usr/bin/vmplayer
In the following dialog, you can choose a .vmx file (virtual machine format from VMware). This file describes which kind of virtual machine you want to start and contains the necessary configuration — for example, the location of your virtual disk, memory size, and some basic hardware setup information. According to your selection, a guest virtual machine is started, and you can interact with it like with a "normal" computer system. Presumably you will not notice any difference between this virtual machine and a real machine; the virtualization is transparent. Furthermore, you can easily share such a virtual machine with others.
In addition, VMware's Technology Network (VMTN) provides technical and community resources for you. You can download prebuilt virtual appliances at http://www.vmware.com/vmtn/appliances/ and use them with the VMware Player. For example, you can download a preconfigured virtual machine that is configured for web browsing. By using this virtual machine for surfing the World Wide Web, you are safer from attacks by malicious websites. Such a website can only compromise the virtual machine, and all your private data that reside on the host machine are safe. Many other specialized virtual machines are available at the VMTN; just visit the website and explore the different appliances.
Please note that you cannot create your own virtual machines with the software provided by VMware, but you can execute a given guest virtual machine. However, we will show in Section 2.2.4 how you can build your own virtual machines with the help of third-party software.
With the VMware Server software, you can also create your own guest virtual machines that you can then use as virtual honeypots. The installation process is similar to the one for the VMware Player and requires three steps:
1. | You find the download link at http://www.vmware.com/download/server/. You should fill out a short survey before proceeding to the next step. |
2. | Before you can download the software, you must log in. If you already have an account, sign in. If not, create an account and register at the VMware website. Afterward, you should read the Agreement to use the software and, if you accept it, agree to the terms. Then you can start the downloading process by choosing the appropriate version for your host system. For Windows systems, you should download the VMware Server for Windows Operating Systems version and for Linux systems the Download VMware Server for Linux version in either RPM or tar.gz format. In addition, you should also download the client package for your operating system so that you have an additional option to interact with your VMware Server. |
3. | Depending on the version of VMPlayer you are going to use, do one of the following:
|
To start the VMware Server under Windows, double click on the icon and then the software will start up. For Linux, execute the command
$ sudo /etc/init.d/vmware start
The main interface of VMware will start, and you should make yourself familiar with the different possibilities. In the following, we show you how to create a virtual high-interaction honeypot with VMware. Please note that VMware offers many more possibilities. For more options, please consult the VMware documentation, since this is out of the scope of this book.
At this point, you should have a running VMware Player or VMware Server. We are now going to set up a virtual honeypot within our guest virtual machine. In the first step, we install a basic operating system. This process is very similar to installing an operating system on a normal, physical machine. In the second step, we install some additional software at the host and guest system to enable a flexible way to collect information about information entering and leaving the honeypot. And in the last step we show how you can set up multiple honeypots to create a virtual honeynet.
If you use VMware Server or (an evaluation version of) VMware Workstation, you can create a guest virtual machine on your own. Choose File, New, Virtual Machine, or press CTRL + N to start the configuration process. Follow the on-screen instructions from the configuration wizard to configure the basics of your new virtual machine. You can accept the recommendations of the configuration program to obtain a flexible system. The only exception is the Network Type. Choose "Use network address translation (NAT)," since we will set up a virtual honeypot using NAT first. Later on, we will change the network type to bridge mode to enable full network access for the virtual honeypots.
Once this is done, you have a skeleton of a virtual machine. Now you can install an operating system within this system. You have two options for the installation process: Either you use a bootable Windows 2000 CD-ROM or a CD-ROM with your OS of choice. After having inserted the CD-ROM, boot up the virtual machine, and the installation process starts. The second option is to use an ISO image of an OS. You can configure your virtual CD-ROM drive to treat a given ISO image as a normal CD-ROM. To configure this, choose Commands, Edit virtual machine settings at the main status window. Then select the CD-ROM drive, and change the connection to use an ISO image. Afterward, this ISO image is treated as if it would be a real CD-ROM drive.
If you now start this virtual machine, the installation process begins. Install the operating system within the guest virtual system like you would install it on an ordinary computer. After all, the virtualization software provides you with virtual hardware that is (almost) indistinguishable from a real computer system. To continue our example, please install Windows 2000 within the guest virtual system.
With the VMware Player software alone, you are only able to execute a given guest virtual machine with a .vmx file (virtual machine format from VMware). In this section, we show you how to create your own virtual machines with the help of the open source software QEMU, a free emulator available at http://fabrice.bellard.free.fr/qemu/. With this software, you can achieve similar results as with VMware. However, VMware is easier to use and offers more flexibility, whereas QEMU emulates a real computer system. These instructions to use QEMU in order to build a virtual machine were first published in a slightly different form at http://www.hackaday.com/.
QEMU itself is also virtualization software and capable of most of the features VMware Workstation offers (snapshots, multiple guest virtual machines, and more). It is released under the terms of the GNU Public License (GPL), and thus you can freely distribute it. We advise you to also use the QEMU Accelerator since it increases the performance of QEMU significantly. You can find more information about this accelerator at http://fabrice.bellard.free.fr/qemu/kqemu-doc.html. Binary packages of QEMU for Windows (http://www.h7.dion.ne.jp/~qemu-win/) and Mac OS X (http://www.kju-app.org/kju/) are also available. Moreover, you can find many ready-to-run images of QEMU virtual machines with a free operating system at the Free OS Zoo (http://www.oszoo.org/).
We now describe the process of using QEMU to configure a virtual machine file for VMware. First, you have to install QEMU itself. If you are using Windows, you can download the latest version from http://free.oszoo.org/ftp/qemu/win32/release/. After the download has finished, double click the installer and follow the on-screen instructions. If you are using Linux, you have two options. First, if your distribution offers QEMU, you can use the package manager and install it. For example, if you are using Debian, you can install QEMU via
$ sudo aptitude install qemu
Second, you can install QEMU from its source. Download the latest version from http://fabrice.bellard.free.fr/qemu/download.html and install with the usual command sequence:
$ tar xzvf qemu-VERSION.tar.gz $ cd qemu-VERSION $ ./configure $ make $ sudo make install |
To create your own virtual machine files, you need the qemu-img.exe program (Windows) or the qemu-img program (Linux), respectively. The following command will create a VMware disk file for you:
C:\Program Files\Qemu>qemu-img.exe create -f vmdk WindowsXPPro.vmdk 4G Formating 'Win200Pro.vmdk', fmt=vmdk, size=4194304 kB
Please note that this command sequence is for the Windows version of QEMU. The Linux version is similar — just ignore the .exe extension.
A file "Win2000Pro.vmdk" with a maximum disk size of 4G has been created. Since this is a dynamic growing file system, the actual file is less than 1MB in size for now. You should move this file to the directory where you store your virtual machine files.
In the next step, we create the .vmx file that stores information about the guest virtual machines and is used to configure various parameters. Open your favorite editor and create a file with the name "Win2000Pro.vmx." Insert the following content to create a new virtual machine:
Code View: config.version = "8" virtualHW.version = "3" # We use the filesystem we created in the previous step ide0:0.present = "TRUE" ide0:0.filename = "Win2000Pro.vmdk" ide0:0.redo = "" # The size of the virtual memory we want to use memsize = "512" MemAllowAutoScaleDown = "FALSE" # We use the physical CD-ROM drive of the host systemide1:0.present = "TRUE" ide1:0.fileName = "auto detect" ide1:0.deviceType = "cdrom-raw" ide1:0.autodetect = "TRUE" ide1:0.startConnected = "TRUE" # We disable the support for a floppy drive floppy0.present = "FALSE" # Enable the Ethernet interface, the USB controller, and # the sound support ethernet0.present = "TRUE" ethernet0.addressType = "generated" ethernet0.generatedAddress = "00:0c:29:42:23:0a" ethernet0.generatedAddressOffset = "0" usb.present = "TRUE" sound.present = "TRUE" sound.virtualDev = "es1371" # This is the title display in the VMware Player window displayName = "Windows 2000 Professional" # We use Windows XP Professional as guest virtual system guestOS = "win2000Pro" # Name of the memory file created while running VMware Player nvram = "Win2000Pro.nvram" MemTrimRate = "-1" # Internal configuration uuid.action = "create" ols.syncTime = "TRUE" checkpoint.vmState = "" |
The configuration file defines all components of your virtual machine. Options like the amount of virtual memory, CD-ROM drive, or network configuration are set. The comments inside the file explain what each section is about and should be enough to make you familiar with the structure of such a .vmx file.
Now all prerequisites are fulfilled to start the installation process. Insert your Windows 2000 Professional CD-ROM in the CD-ROM drive and then double click on the file you just created. Now the VMware Player will boot from the CD-ROM, and you can install Windows 2000 Professional within the guest virtual system.
Some further tips and tricks to configure your guest virtual machine:
If you want to boot from an ISO image instead of the physical CD-ROM drive, just change the configuration in the .vmx file in the following way:
Windows— assuming that the ISO image is available as C:\Program Files\Qemu\Win2K.iso:
ide1:0.present = "TRUE"
ide1:0.fileName = "C:\Program Files\Qemu\Win2K.iso" # path
to ISO image
ide1:0.deviceType = "cdrom-image" |
Linux— assuming that the ISO image is located under /opt/qemu/Win2K.iso:
ide1:0.present = "TRUE" ide1:0.fileName = "/opt/qemu/Win2K.iso" # path to ISO image ide1:0.deviceType = "cdrom-image" |
If you want your VMware virtual machine to start in full-screen mode upon start up, add the following parameter to the preceding configuration file:
gui.fullScreenAtPowerOn = "TRUE"
Now you can switch from full-screen mode back to normal window mode with the key-combination CTRL+ALT. However, you cannot switch back to full screen again — a limitation of the VMware Player software.
At http://www.easyvmx.com or http://www.dcgrendel.be/vmbuilder/ you find different online tools with which you can dynamically create .vmx files according to your preferences.
If you are a more experienced user, you can also use QEMU instead of VMware Player or VMware Server, since QEMU offers most of the functionality we need for our virtual honeypot. In Section 2.4.2 we will take a closer look at QEMU in conjunction with Argos.
You now have a guest virtual machine with a running instance of Windows 2000 Professional. In the next step, we install some additional software at both the host and guest system that allows us an extended monitoring of what is going on at our honeypot. With the help of these additional tools, we are able to closely monitor our honeypot. This mainly aids in the day-to-day handling of the honeypot and for forensics. The extended logging data lets us collect more information about what is going on at the system.
At the host system, we can monitor several aspects. First, we can capture all network data entering and leaving the honeypot system. Since all this data passes through the host system, we can use tcpdump or Wireshark/Tshark at the interface used to connect the guest virtual system to the network. We thus capture all network communication of the honeypot and can use this information later on to study attacks. This process is transparent for the honeypot systems, and there are no indications left that reveal this monitoring.
Moreover, you should also enable a firewall on the host system. Imagine that a piece of autonomous spreading malware compromises your Windows honeypot. Presumably, it then tries to propagate further by attacking other systems. Since you do not want other systems on the Internet infected by this piece of malware, you should block outgoing, malicious connections ("extrusion prevention"). As an additional layer of defense, you can also enable an inbound firewall on the host system that blocks access to common ports used by autonomous spreading malware. As a best practice, we advise you to block both ingoing and outgoing traffic on TCP and UDP ports 445, 135, 139, and 1025 to mitigate the risk involved. These ports are commonly used by Windows-based machines for different tasks (e.g., remote procedure calls) and had several critical security vulnerabilities in the past. By blocking outgoing traffic on these ports, you can make sure that your honeypot will not attack other vulnerable systems located elsewhere on the Internet on these ports. By blocking inbound connections, you make sure that no "boring attacks" happen at your honeypot. In addition, you can also install an IDS like Snort (http://snort.org) on the host system to learn more about the actual attacks against your honeypot. We will not cover this process in more detail for now. In Section 2.5 we introduce a powerful approach to safeguarding your honeypot that enables this kind of protection system.
In the previous section we briefly introduced several methods to collect additional information at the host system. This provides more information about cyber attacks, but the most valuable information can be collected at the honeypot itself — within the guest virtual machine. If we are able to closely monitor this system, we can, for example, observe what the attacker is typing, which tools he is executing and how he is escalating his privileges. Here is another example of why we must closely monitor the virtual honeypot: Imagine that the attacker uses an encrypted session via SSH to connect to the honeypot. If he then downloads additional tools via an SSL-encrypted website, the network dumps collected at the guest system are pretty useless. Since the complete session is encrypted and we do not know the correct key to decrypt the network stream, the tcpdump logs are rather useless to us. However, if we can observe the keystrokes and everything else at the honeypot itself, we can see which commands the attacker executes within the SSH session and which tools he downloads from the SSL-encrypted website. This way we can learn more about his procedures and study the attacker in more detail.
At the guest system, we are going to install the tool Sebek, which can collect all the necessary information to reconstruct what exactly the attacker did on the honeypot. With it we can overcome the limitations of simple network logging at the guest system and other drawbacks, as just pointed out. Sebek is developed by the Honeynet Project and is available at http://www.honeynet.org/tools/sebek. We will discuss Sebek in more detail in Section 2.5.1. For now, you can think of Sebek as a mechanism that transparently captures information about everything that happens at the honeypot system. Basically Sebek helps us to closely monitor the inner status of the honeypot.
Download the latest version of Sebek from http://www.honeynet.org/tools/sebek. Choose the version for Windows-based system and download it to your guest virtual machine. Then execute the binary and follow the on-screen instructions. You have to answer a few questions and then reboot the virtual machine. Afterward, your honeypot is equipped with Sebek, and you can easily collect a huge amount of information. To leave no signs of Sebek on the honeypot system, delete the downloaded installer and empty the trash can of your Windows 2000 installation afterward.
We introduced the different network capabilities of VMware in Section 2.2.2. In our current setup, the guest virtual machine uses NAT networking, and therefore it is not reachable by other systems on the Internet. We have chosen NAT networking for test purposes. You can safely play around with your honeypot without fear that an attacker might compromise the system while you are experimenting with it.
Now we want to connect our honeypot to the real Internet. First, shutdown the guest virtual machines and then choose Commands, Edit virtual machine settings at the main status window. In the configuration window you see the settings from the Ethernet adaptor. Change the settings from NAT networking to Bridged Networking and click the OK button. Now your guest virtual machine will use bridged networking in the future.
Before you power on your honeypot, make sure that you have a second IP address the honeypot can use. Either your ISP can provide you with one or, if you are setting up the honeypot within a corporate environment, consult your network administrator. Read Section 2.5 carefully to learn how to safeguard your honeypot. This helps you to mitigate the risk involved when running such a system.
Once you have configured a safeguard for your honeypot, boot up the guest virtual machine and configure the Windows honeypot to use the second IP address. Make sure that your honeypot can reach other systems on the Internet and also that other systems can reach your honeypot. Now your honeypot is live — that is, it receives malicious network traffic and collects information about malicious activities. Congratulations!
Until now, we have set up a virtual high-interaction honeypot based on Windows 2000 Professional. However, it is also possible to build a whole virtual high-interaction honeynet — that is, a network of honeypots. The process is easy: Just repeat the steps we have outlined in Section 2.2.4 to set up additional guest virtual machines. You can then configure these machines as honeypots, similar to the steps described in that section. The different guest virtual machines can then interact with each other and form a high-interaction honeynet.
How you configure your honeypots depends on what you want to achieve. For example, if you are interested in attacks against Windows systems, install Windows in the configuration you are interested in. However, if you want to observe attacks against Linux servers, set up your honeypot as a "normal" Linux server and connect it to the Internet. Another approach is to install software on the honeypot that has vulnerabilities that were published in the preceding few weeks or months. For example, if a new security advisory is published for a popular web application, you could set up a honeypot with just this particular web application and then observe attacks against it.
With a virtual high-interaction honeynet you can even collect more information about the tools, tactics, and motive of attackers. You can study attacks against different operating systems or different network services. In addition, you can observer how attackers proceed on different kinds of systems and which tools they use. With the virtual approach it becomes easy to manage the honeynet. You can dynamically add or delete honeypots from the honeynet or, by simply resetting the virtual machine, rebuild parts of the honeynet. Per guest virtual machine you should reserve at least 256MB RAM, but 512MB RAM is better. This gives the guest system enough memory to interact with, and they run more fluently. Thus, the underlying host system should be equipped with a rather large amount of memory, preferably at least 1GB.